Four Ways To Manage Small User Communities in Minutes Per Month.
As small and medium enterprises (SMEs) come to depend more on Software as a Service (SaaS) tools, they often find themselves running into problems managing an ever-changing cast of internal employees and external marketing partners.
And this challenge—known to IT professionals as “Identity and Access Management” (IAM)—rears its head surprisingly quickly: not just when your user community breaks triple digits, but often when it passes more than just a dozen or so users.
There’s a natural tendency for SME system admins to avert their gaze from IAM issues; after all, you have lots of bigger fish to fry. But in today’s world, even the smallest organizations are responsible for providing proper protection of the customer and employee data their systems house. And that means you either have to deal with IAM—or run the risk of a potentially serious data breach.
The good news is that you don’t have to be an information security expert to handle small-system IAM chores in a responsible way. In this post, we suggest five features you should look for in your SaaS platforms to help meet that goal, and ways to leverage those features to get the best security bang for your administrative burden.
User Approval
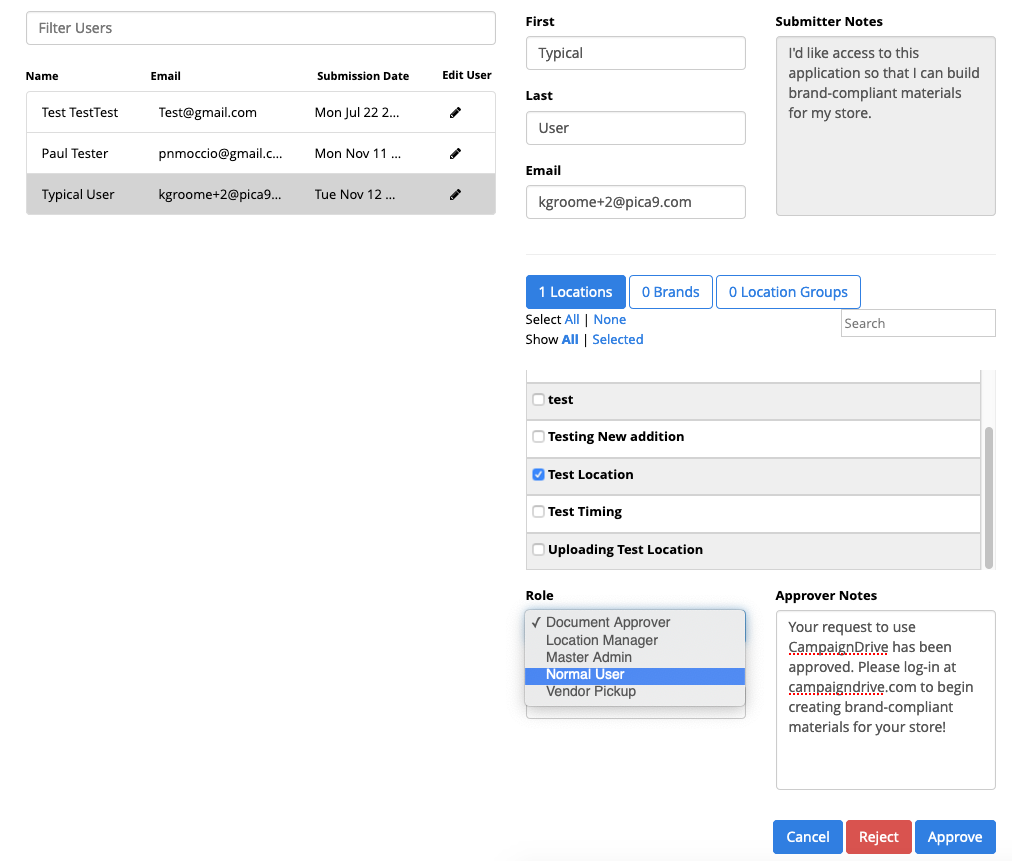
User Approval in CampaignDrive takes just a couple clicks, and allow you to segment users geographically, by brand, and by User Role.
With a small user community, each user is an especially important stakeholder. It helps enormously to give them a simple, web-based way to request and be granted the access they need. When considering SaaS solutions, inquire about the access approval process, and probe to see if there are multiple options for handling this important moment in the user’s lifecycle. When the community is small, you may want to approve each user manually. As you grow, you may want to segment your user community so that approval chores can be shared among a team. At the next level up, you might want to route specific users to specific approvers based o a brand or regional basis. Still later, you may opt to welcome users in without approval, but only for a limited-capability role.
Parking Lots
With smaller communities, you may find that you need to pause user accounts without necessarily deleting them. For example, when an employee goes on maternity leave, or an extended sabbatical, they may want to have their access to the system preserved, while you want to ensure that a temporarily dormant account doesn’t come to represent a security risk. To handle this chore, ask your vendor if the system has a method to “park” accounts, so that they can be reactivated quickly and easily. This can take many different forms, so just make sure that you’re comfortable with the method—before you run into the need!
Configurable Roles and Permissions
Even in very small communities, there will be actors who are highly trusted, and those who are granted only limited capabilities. Make sure that your SaaS system allows you to define capabilities at a granular level. Take care to start with a manageable number of different roles, and set aside time a couple times a year to look at each user role to (a) see that you have a sufficient number of users assigned to the role to justify the management overhead; and (b) verify the behavior of users in that role is in line with your expectations.
User-Based Transaction Reporting
The more detail you can discern at the user level with your system’s reporting tools, the better able you’ll be to handle the IAM burden over time. Remember that user skills and familiarity with the system will increase with time; this may lead you to offer greater capabilities within an existing role. But also, keep in mind that ever system has some kind of a learning curve. So be sure to keep track of the behavior of users based on their time on the system. Make sure that your reporting system allows you to drill down to the individual user level, and spend time looking at this data to find your power users within each role.
Over time, of course, if your user community grows, this kind of individual attention won’t be possible. But if you’ve identified some representative users early on, you’ll find that you have a better grip on IAM challenges in later years.






